LI.FI has announced a $29M Series A extension, led by Multicoin and CoinFund. Read Here.

Wormhole – A Deep Dive
All you need to know about Wormhole
Introduction
Today, we’re expanding our knowledge of cross-chain protocols by learning more about Wormhole.
This article examines the design, security, and trust assumptions of Wormhole, highlighting its unique features and tradeoffs by thoroughly analysing its architecture.
Here, we will cover the following:
Wormhole — An Overview
Product Offerings
Network Effects
Security Check
How It Works — Transaction Lifecycle
Trust Assumptions & Tradeoffs
Risk Analysis: Architecture Design & Security Considerations
Community & Resources
Let’s dive in!

Wormhole — An Overview
Launched in October 2020, Wormhole is a messaging protocol designed to enable developers to build cross-chain native applications spanning multiple chains. Wormhole began as a hackathon project with the objective to find a solution to allow blockchains to ‘talk to one another’.
Initially incubated and supported by Jump, the first version of Wormhole (Wormhole V1) was primarily focused on establishing a bi-directional token bridge between Ethereum and Solana. As the project progressed, Wormhole evolved into a generic message-passing protocol that connected several chains in the ecosystem. This evolution aligned with its broader vision of becoming a foundational layer upon which developers could construct diverse cross-chain applications. Consequently, Wormhole V1 was phased out, and Wormhole network was introduced in August 2021.
Product Offerings
Several cross-chain native applications and product offerings have been built atop Wormhole, including products by the Wormhole team itself, in response to the growing needs of a multi-chain ecosystem:
Portal – a lock and mint token bridge that allows users to bridge tokens and NFTs across chains supported by Wormhole. It is one of the first applications to use Wormhole’s messaging functionality and has contributed significantly to its growth.
Connect – a widget that allows developers to integrate a Portal-like interface for token bridging within their application. It gives developers a simple and quick way to add bridging capabilities to their apps.
Gateway – an application-specific blockchain purpose built to improve the connectivity of Cosmos-based appchains with the wider ecosystem. It uses a liquidity router which serves as a unified liquidity layer across Cosmos chains. This tool is beneficial for developers aiming to attract users and liquidity to their Cosmos appchain and for users seeking to bridge funds to the Cosmos ecosystem. Gateway is currently live for developers and available for users via Portal.
Queries – a tool for cross-chain data queries that enables applications to read onchain data from any EVM chain within the Wormhole ecosystem. This data is verified by a ⅔ supermajority of 19 Wormhole Guardians. This product is still in the early stages of development with Synthetix expected to be an early adopter.
These products are further bolstered by multiple developer friendly solutions and features by the Wormhole team (many of which are now built and maintained by contributors of the newly formed Wormhole Foundation) such as:
xAssets – assets that can be bridged across any Wormhole supported chain without any slippage. Example: Pyth Network recently launched their $PYTH governance token as a Wormhole xAsset, making it accessible for users across 27 chains.
Automatic relayers – a network of relayers that can deliver messages across any Wormhole supported chain. This feature allows developers to build cross-chain applications on Wormhole without the need to setup and maintain their own off-chain relayers.
Wormholescan – a cross-chain block explorer and analytics platform covering the Wormhole ecosystem. This tool can be used to track cross-chain transactions and understand the network activity across the Wormhole ecosystem.
Network Effects
Given Wormhole's early and continued focus on the Solana ecosystem, it's not surprising that Solana ranks as the most actively used chain on Wormhole in terms of number of transactions.
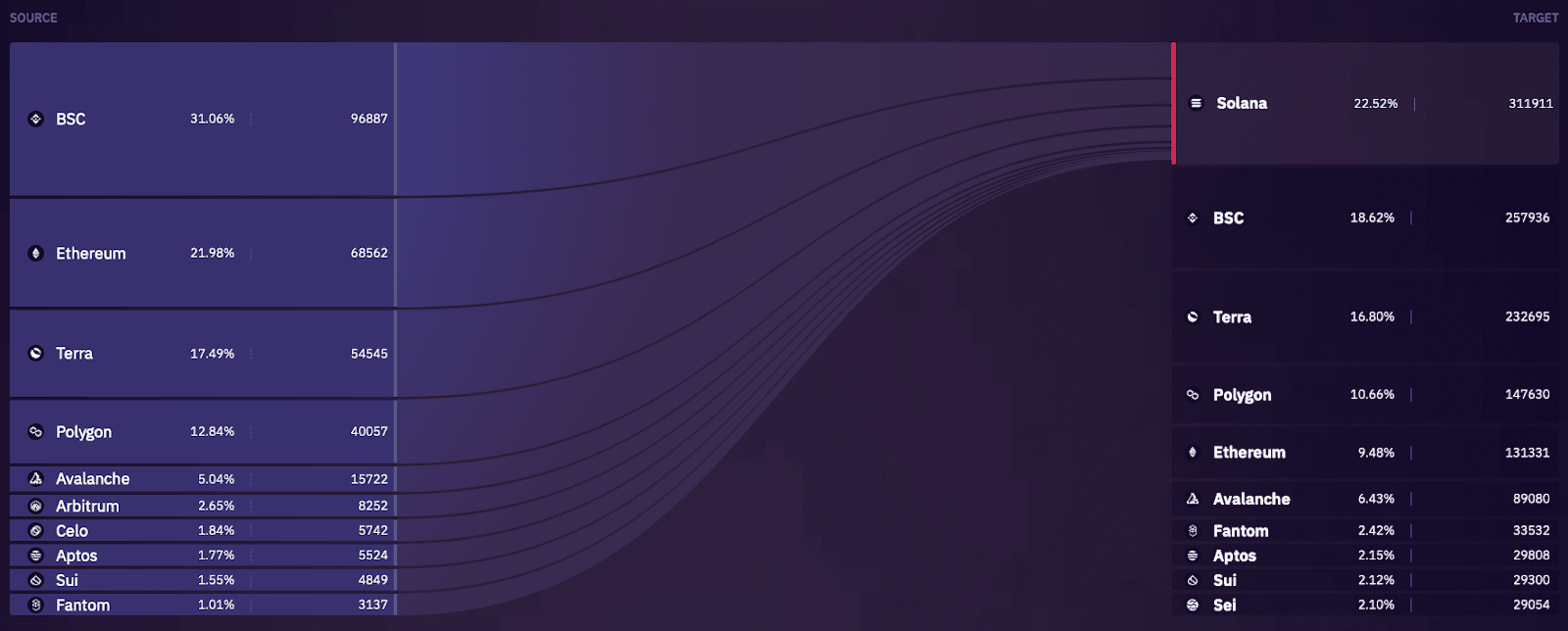
Factors contributing to Wormhole’s growth and positioning as one of the top messaging bridges in the ecosystem include:
200+ projects building on Wormhole – Wormhole has established significant distribution in the ecosystem with several applications using it to build apps for use cases like liquidity bridges (Allbridge, Mayan, Magpie), multi-chain tokens (PYTH), token standards (Nexa), in-app bridging with Connect (Astroport, Uniwhale, YouSUI), cross-chain deposits (Friktion, PsyOptions, Aftermath Finance).
Wormhole x NFTs – Wormhole’s cross-chain NFT standard was popularly used by Dust Labs to migrate their NFT collections DeGods and y00ts from Solana to Ethereum and Polygon respectively. This NFT standard is also used by the Aptos NFT bridge to allow developers and users to bridge NFTs to/from the Aptos network.
Wormhole’s $50M ecosystem fund – the $50M ecosystem fund offers the much needed financial support to developers building cross-chain applications that leverage Wormhole’s messaging infrastructure. Managed and operated by Borderless Capital, this fund draws on funding support from notable investors including Jump Crypto, Polygon Ventures, and the Solana Foundation, among others.
xGrant program – In early 2023, Wormhole introduced the xGrant program, designed to support developers, researchers, and founders. This initiative provides not just financial assistance, but also mentorship and resources to facilitate the development of innovative projects. The grants cover various expenses such as software development, marketing, team costs, and other aspects of project growth and expansion.
Bitcoin on Solana with tBTC – Threshold Network introduced tokenized Bitcoin (tBTC) on Solana using Wormhole to mint the asset. This marked tBTC’s first expansion to a non-EVM ecosystem and enabled users to use Bitcoin in the Solana DeFi ecosystem.
Wormhole x Uniswap – Wormhole’s positioning as one of the secure messaging bridges in the ecosystem got a significant boost with Uniswap’s Bridge Assessment Committee endorsing Wormhole for all cross-chain deployments, following a comprehensive evaluation of six different bridges. Additionally, Uniswap's active use of Wormhole for cross-chain messaging, particularly with chains like Celo, further solidifies Wormhole's standing as a dependable choice for secure messaging needs.
Wormhole x Circle CCTP – Wormhole has successfully integrated Circle's Cross-Chain Transfer Protocol (CCTP), making it accessible to other applications through Connect and to users via Portal. The anticipated launch of CCTP on Solana is generating significant interest, with teams like Jupiter already declaring their plans to support it in their applications through Wormhole.
Wormhole’s $225M funding round at a $2.5B valuation – Wormhole recently secured a significant funding milestone, completing a $225 million round at a valuation of $2.5 billion. This substantial investment underscores the strength of Wormhole's team, the widespread adoption of its product, and the overall quality it offers.
Security Check
Audits – Wormhole’s architecture consists of several key components like the Guardian nodes and smart contracts for different chains and execution environments. The various parts of their tech stack have undergone 22 audits in total.
Bounty – Since September 2022, Wormhole has run a $2.5M bounty program on Immunefi, primarily focusing on the security of Wormhole's smart contracts and Guardian nodes
Security Breach – In February 2022, Wormhole network experienced a security breach as an attacker ‘exploited a signature verification vulnerability in the Wormhole network to mint 120k Wormhole-wrapped Ether on Solana’, resulting in an estimated loss of approximately $326 million. The vulnerability was fixed within a few hours and Wormhole was back online shortly after, with Jump providing necessary funds to cover the shortfall.
Following the exploit, the Wormhole team announced the following security initiatives for the future:
Continuous audits – comprehensive and ongoing audits of the Wormhole codebase have been conducted and planned to prevent future vulnerabilities.
Advanced monitoring tools – features like accounting mechanisms and monitoring tools to isolate risks across chains and detect threats early to ensure dynamic risk management is possible.
Bug bounty program: Wormhole launched a bug bounty program on Immunefi, which was launched soon after the exploit.
In light of these security upgrades, Uniswap’s Bridge Assessment Committee acknowledged Wormhole's efforts in their report, stating:
“Subsequent to the exploit, Wormhole has made substantial enhancements to its practices such as improved implementation processes, clearer incident response plan and robust unit testing. These improvements are commendable and demonstrate the protocol's growth and maturity.”
Wormhole has added several security features to its stack including:
Global accountant – this tool monitors the total circulating supply of all Wormhole assets across all chains. Essentially, it prevents any blockchain from moving around more assets than they are actually allowed to.
Governor – Complementing the Global Accountant, the Governor tracks the inflows and outflows of assets across all chains. It has the authority to delay suspicious transfer and limit the impact of exploits by enabling Guardians to hold Wormhole messages for 24 hours if their value is excessively large. It can also be used as a rate limit for the notional flow across a chain. Additionally, it serves as a rate limiter for notional flow across chains, which is particularly beneficial for newer, less tested chains. The Governor's limits can be adjusted as a chain's ecosystem matures.
Open-source repositories – By making its code repositories open-source, Wormhole effectively lowers barriers for white-hat hackers to identify and report vulnerabilities.
Comprehensive monitoring via Guardians – Wormhole Guardians are specialised validator companies with expertise in running, monitoring, and securing blockchain operations. They continuously track activity at the blockchain and smart contract level and ensure security of the Wormhole network via tools like the Governor.
ZK coming to Wormhole – Wormhole is actively working on integrating ZK verification for messages to its stack.
How It Works — Transaction Lifecycle
The process of transferring messages from a source chain to a destination chain via Wormhole's architecture is intricate yet straightforward at a high level. Here's a simplified breakdown:
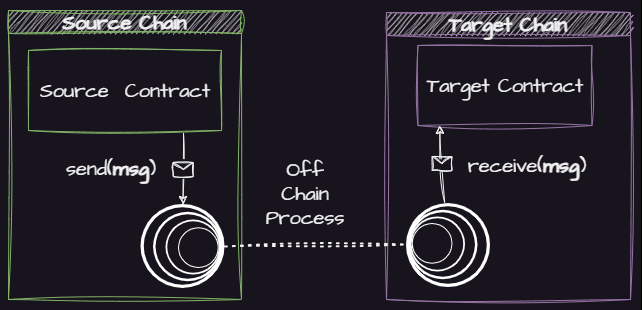
1) Emission of Message: Each message originates from a 'Core Contract' on the source chain.
2) Verification and Signing by Guardians: This message is then authenticated and signed by 19 Guardians in an off-chain process. A message is considered authentic only if it receives signatures from at least 2/3rds (13 out of 19) of the Guardians.
3) Relay to Destination Chain: Once verified and signed, the message is relayed to the Core Contract on the destination chain.
Looking more closely, we see several key components working together to ensure secure cross-chain messaging:
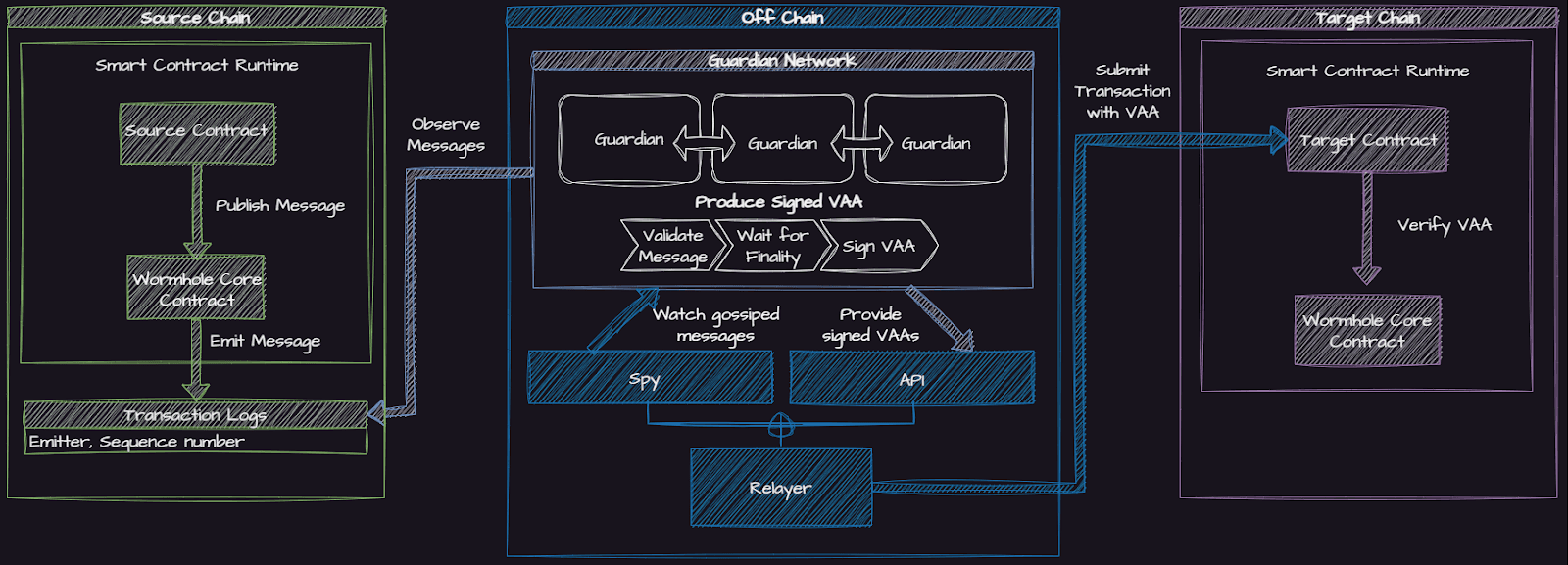
Let’s dive deeper into how messages are verified by Wormhole’s Guardian network:
Step 1: The Core Contract on the source chain emits the message.
Step 2: Guardians observe and verify the message's authenticity.
Step 3: The Guardians wait for the finality of the source chain before signing the hash of the message body, attesting to its validity.
Step 4: The signatures from each Guardian are compiled into a multisignature document known as the Verifiable Action Approvals (VAAs).
Step 5: Relayers then transfer the VAA to the Core Contract on the target chain.
Note: the ‘Spy’ observes all messages passing through the Guardian network and records them in a storage system, like an SQL database, for analysis and further use.
Trust Assumptions & Tradeoffs
Here’s a list of notable trust assumptions and tradeoffs made by Wormhole:
External verification by a set of validators – Wormhole’s proof-of-authority system inherently trusts that Guardians can be trusted to verify transactions and that over 2/3rd of Guardians will not collude at a certain time. In case the majority of Guardians collude, users’ funds could be stolen.
Censorship risk – 7/19 Guardians can collude to censor messages.
No slashing mechanisms for Guardians – In Wormhole's system, there is no bonding or slashing mechanism implemented for the Guardians. However, accountability is a key aspect of the network's design. Any malicious activity can be directly traced back to the specific Guardian. This direct attribution means that in cases of fraud or misconduct, the involved Guardian could potentially face legal liabilities and suffer significant reputational damage.
Permissioned Guardian network – Adjustments to the Guardian set, whether it involves adding new Guardians or removing existing ones, are governed by a 13/19 signature scheme.
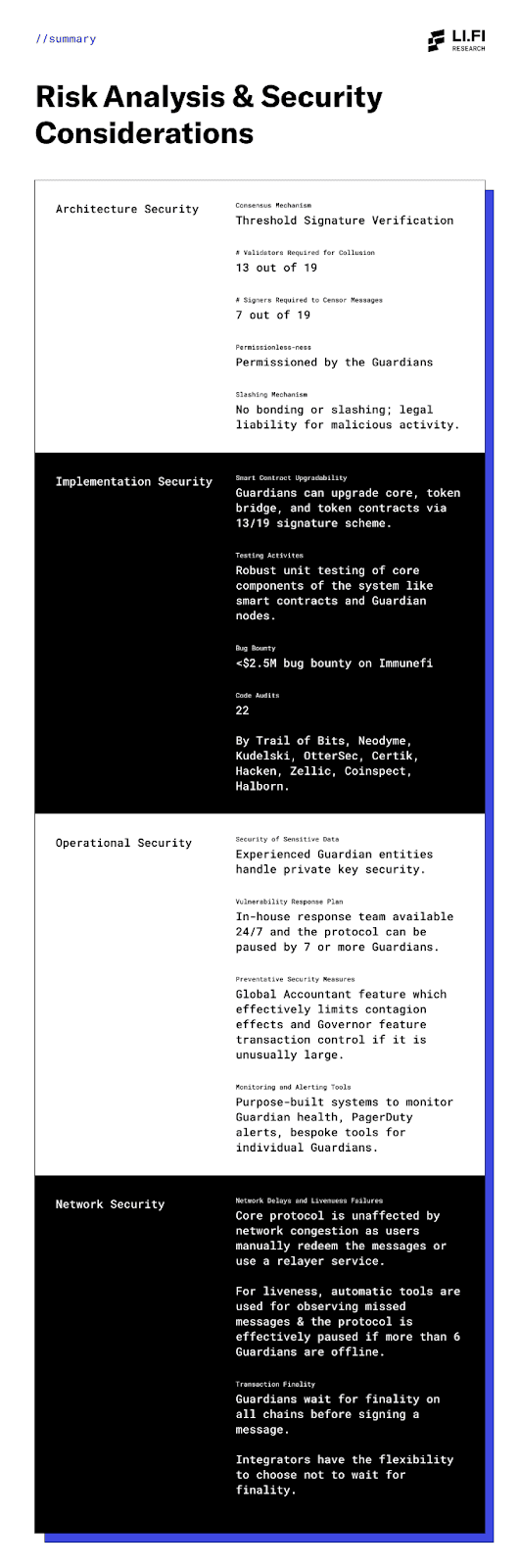
Risk Analysis: Architecture Design & Security Considerations
Community & Resources
You can learn more about Wormhole through the following:
You can stay updated about its community by following them on:
FAQ: Wormhole – A Deep Dive
Get Started With LI.FI Today
Enjoyed reading our research? To learn more about us:
- Head to our link portal at link3.to
- Read our SDK ‘quick start’ at docs.li.fi
- Subscribe to our newsletter on Substack
- Follow our Telegram Newsletter
- Follow us on X & LinkedIn
Disclaimer: This article is only meant for informational purposes. The projects mentioned in the article are our partners, but we encourage you to do your due diligence before using or buying tokens of any protocol mentioned. This is not financial advice.