Symbiosis — A Deep Dive
All you need to know about Symbiosis
Symbiosis, a cross-chain liquidity protocol, has been integrated into LI.FI and is available to our partners via the SDK, API, and widget. Users can now find routes supported by Symbiosis on Jumper.
Today, we’re expanding our knowledge of cross-chain protocols by learning more about Symbiosis.
This article reviews Symbiosis’ design, security, and trust assumptions. We'll discuss what makes it different and consider the benefits and compromises of its design.
Here, we will cover the following:
Symbiosis – An Overview
Bridge Design – Architecture and How it Works
Bridge Design Analysis: Advantages, Trade-Offs and Trust Assumptions
Supported Chains
Team
Community
Let’s dive in!
Symbiosis – An Overview
Symbiosis, launched in early 2022, is a cross-chain DEX that uses an onchain liquidity pool system to enable the exchange of assets across chains. It uses the automated market maker (AMM) model to balance liquidity for trading between pools on various chains.
Furthermore, Symbiosis uses the Boba BNB chain as a service or host chain, which is referred to as the s-chain in Symbiosis' documentation. All transactions within Symbiosis are processed via the s-chain, which is a crucial component of the protocol's design as it enhances the protocol’s functionality and operational efficiency.
In particular, through its cross-chain AMM DEX, Symbiosis offers the following functionalities:
Cross-chain swaps – users can exchange any token pair across the chains that Symbiosis supports.
Farming – users can earn yield on assets by adding them to Symbiosis’ liquidity pools across chains within the Symbiosis network.
Additionally, Symbiosis offers the ability to send information across chains and execute contract calls on different chains. When combined with bridging and cross-chain swaps through liquidity pools, these capabilities enable more sophisticated cross-chain operations, such as:
Cross-chain zaps – users can supply liquidity to pools on lending/borrowing protocols, liquid staking / staking platforms, Symbiosis’ pools, easily in a single transaction from any asset on different chains. For example, a user holding USDC on Optimism can directly get exposure to stETH with Lido on Ethereum in one transaction.
Bridge Design – Architecture and How it Works
The architecture of Symbiosis consists of two main elements: onchain and off-chain components. The onchain aspect consists of smart contracts deployed across various chains, while the off-chain part is made up of a peer-to-peer (P2P) relayer network.
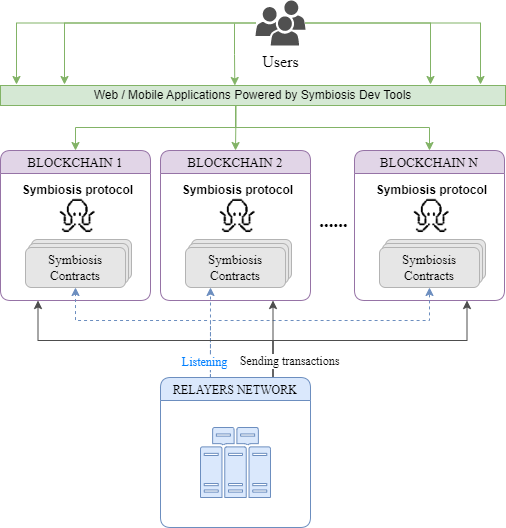
Now, let's examine these two components in more detail:
Onchain Smart Contracts and sTokens
To facilitate cross-chain interactions, Symbiosis deploys non-custodial smart contracts on three different chains:
The source chain – this is the chain where the users' assets are held before initiating the cross-chain transfer.
Boba BNB (Symbiosis’ service blockchain, also known as the S-chain) – It hosts essential components of Symbiosis, including smart contracts with mint-burn logic and 'Octopools' (liquidity pools).
The destination chain – this is the chain where users’ assets are sent to complete the transfer.
Every time a user does a cross-chain transfer via Symbiosis—meaning they’re moving assets from the source chain blockchain to the destination chain—it goes through this Boba BNB service chain, also known as the S-chain.
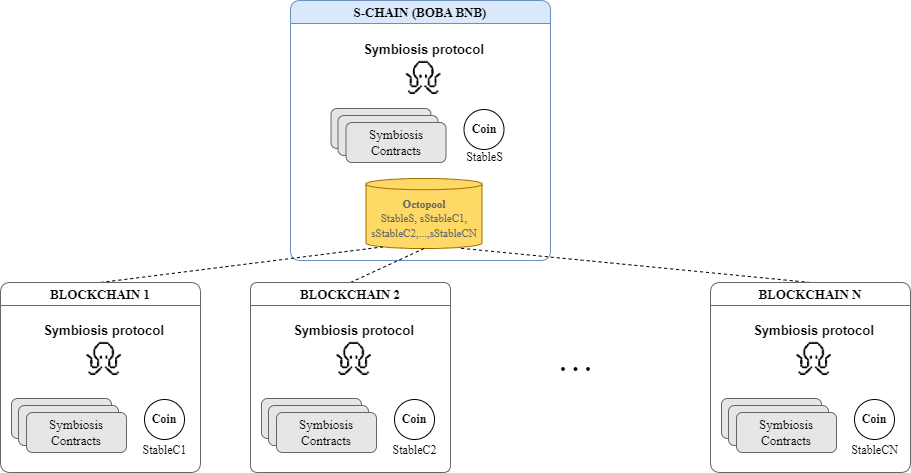
Symbiosis also introduces sTokens, which are synthetic tokens that act as transit tokens on the s-chain to streamline the cross-chain transfer process.
sTokens represent the value of an asset on the S-chain. For instance, Symbiosis creates sTokens for stablecoins like USDC, BUSD, and USDT, as well as WETH and WBTC on some chains, due to their widespread use and stable value across chains.
To better understand the role of sTokens and the S-chain in Symbiosis' transaction process, let's consider some specific examples:
Example 1: Exchange USDC on Ethereum for BUSD on the BNB chain.
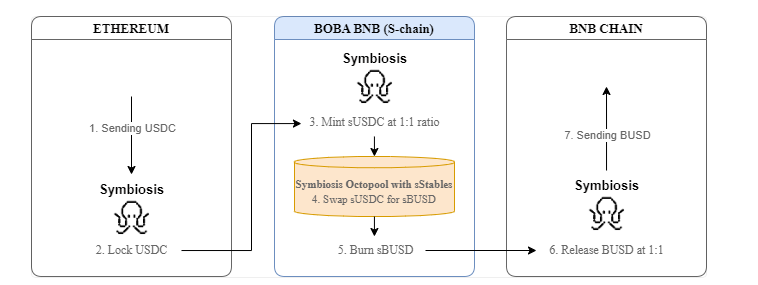
Step 0 – User gives approval for USDC on Ethereum (to the MetaRouterGateway contract).
Step 1 – User sends USDC to Symbiosis’ Portal contract on Ethereum.
Step 2 – The USDC is locked in the Portal contract.
The BridgeV2 contract, deployed on each blockchain that Symbiosis supports, sends important information about the burning and minting actions involved in the cross-chain transfer to and from the off-chain Relayer network.
Upon receiving this information, the Relayer network validates the information, signs it, and then forwards it to the s-chain.
Step 3 – sUSDC are minted at a 1:1 ratio with the tokens locked in Portal (this is done via Synthesis contracts on the S-chain).
Step 4 – Symbiosis Octopool, an AMM on Boba BNB with pools for sStable tokens and sWETH tokens, swaps the sUSDC for sBUSD (the required token on the destination chain).
Step 5 – An equivalent amount of sBUSD is burned (this is done via Synthesis contracts on the S-chain).
This is done to maintain the number of sBUSD in circulation, as the sTokens’ supply must correspond to the actual assets. And since BUSD will be given to the user in this cross-chain transfer, the corresponding sBUSD on the S-chain are no longer needed to represent that asset.
The information about the burn event is sent to the destination chain contracts via the Relayer network.
Step 6 – BUSD is released at a 1:1 ratio with the sBUSD burned on the S-chain.
Step 7 – The BUSD is sent to the user’s wallet on the BNB chain.
A similar process is carried out if a user is exchanging WETH between chains. However, for any assets other than stablecoins and WETH, the token is first swapped into one of these assets before following the same process as described above.
More detailed information about Symbiosis’ core smart contracts can be found here and in-depth technical information on how these different routing contracts interact with each other can be found here.
Off-Chain Relayer Network
The Relayer network is an integral part of the Symbiosis protocol. It is the off-chain component that complements the onchain smart contracts, enabling the protocol to perform its cross-chain functions. Its main purpose is to relay the necessary information for the transfers between chains.
To ensure that relayers operate both efficiently and honestly, the network employs a crypto-economic incentive structure:
Each relayer must stake 100k SIS tokens (this amount will be increased when the network transitions from Proof of Authority to Proof of Stake in the near future) to participate in the network.
Relayers can earn rewards for successfully relaying information and maintaining the integrity of the network.
The Relayer network is organized into distinct groups, each with specific responsibilities:
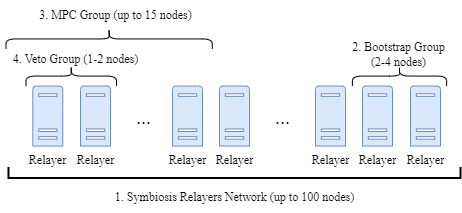
The Relayer network – this is the entire set of Relayers responsible for transferring information across chains. Up to 100 nodes can be part of this network, with the size determined by the Symbiosis administrators. At present, the relayer network is governed by a Proof of Authority mechanism where trusted and experienced entities are appointed as relayers. This group consists of a combination of Symbiosis’ investors, professional node runners, and strategic partners such as Bixin VC and 3Commas, to name a few. Looking ahead, Symbiosis’ relayer network is set to transition from a PoA to Proof of Stake (PoS) framework. This shift will democratize the role of relayer, making it permissionless for anyone to participate as a relayer in the network.
The Bootstrap group – this group includes 2-4 nodes that provide information about the current relayer set to the new Relayers joining the network.
The Multi-Party Computation (MPC) group – this is the group tasked with validating each cross-chain transfer and providing a signature to confirm its authenticity. A transfer requires a signature from two-thirds of the MPC group, which can include up to 15 nodes. As highlighted earlier, this group features reputable entities such as Binance Labs, DWF, Bixin VC and 3commas, among others.
The Veto group – this is a smaller subset of trusted relayers, consisting of 1-2 nodes that must sign every signature generated by the MPC group. Without their signature, the MPC's validation is deemed invalid, and the transfer is not processed.
It's important to understand the connection between a node and a relayer:
A relayer within the Symbiosis network is essentially a node that has been officially registered through the staking smart contract. This means that each unique relayer address corresponds to a single relayer node within the network.
Node runners, who may be individuals or organizations, have the capability to operate multiple nodes, provided they have sufficient funds to meet the minimum staking requirement for each one.
With an understanding of Symbiosis' architecture and its operational mechanisms, we can now examine its benefits, tradeoffs, and trust assumptions.
Bridge Design Analysis: Advantages, Trade-Offs and Trust Assumptions
The cross-chain AMM design of Symbiosis, with liquidity pools on different chains, offers several key advantages:
Liquidity provision for any asset – AMMs allow for the creation of liquidity pools for any asset pair. This flexibility enables Symbiosis to support a wide variety of tokens from different chains.
No single point of centralization – Cross-chain DEXs, in theory, can operate without a central entity managing user funds (as is the case with centralized exchanges) or balancing liquidity across chains (as seen in the intent-based bridge design). Since trades are executed via smart contracts and liquidity is provided by pools rather than individual counterparties, the risk associated with the other party defaulting is eliminated. However, in reality, cross-chain DEXs also introduce third-party entities in their design, as seen in Symbiosis’ case with the off-chain relayer network. This adds its own trade-offs and trust assumptions.
Scalability – AMM DEXs can easily add new assets and liquidity pools across chains without major infrastructure changes. By offering higher yields, users are incentivized to provide liquidity, ensuring adequate liquidity even for niche markets or newly supported chains.
Automated rebalancing – The design of AMMs naturally rebalances pools based on supply and demand dynamics, handling large volumes of trades and liquidity management autonomously. This is crucial for scaling and capital efficiency, though it comes with its own set of limitations.
AMMs are limited by the liquidity they’re able to attract to their pools. While higher demand for liquidity should theoretically lead to increased yields and attract more LPs, the reality is that LPs have many opportunities across DeFi, and cross-chain AMMs may struggle to get sufficient liquidity to support their operations.
Moreover, this design inherently requires capital to be locked into pools, effectively creating a target for hackers as the pool grows in size. This creates a honeypot and presents a big risk of getting drained, as seen in historical bridge hacks. While these incidents have involved messaging bridge protocols rather than liquidity protocols, the risk remains.
The off-chain Relayer network also introduces risks and trust assumptions:
Collusion risk – If two-thirds of the nodes collude, they could potentially pass a fraudulent message and steal user funds.
Loss of funds – There's a risk of losing user funds if nodes lose their private keys.
Censorship risk – Transactions can be censored by a single node from the Veto group or if two-thirds of the nodes in the MPC network decide to do so.
Permissioned relayer network – At present, the Symbiosis relayer network is permissioned, functioning under a Proof of Authority model where only vetted entities are designated as relayers. Additionally, the selection of relayers within the veto group is managed by Symbiosis system administrators. Looking ahead, with the network's planned shift to a Proof of Stake protocol, there is potential for the relayer network, including its various groups, to become permissionless and decentralized.
No slashing mechanism – At present, Symbiosis does not employ a slashing mechanism to deter relayers from engaging in malicious behaviour. Nevertheless, it is assumed that since the relayers are esteemed entities concerned with their reputation, the potential gains from collusion are outweighed by the reputational damage such actions would incur. Furthermore, should a relayer act with malice or become unresponsive, Symbiosis retains the authority to revoke their status within the staking contract.
Considering these factors, we can assess Symbiosis' design and architecture as follows:
Security – In the worst case scenario of collusion between relayers or lost private keys, user funds can be lost. Moreover, there’s also the ever-present smart contract risks and the risk of logic flaw in the pool’s functioning with such designs. However, Symbiosis has undergone 8 audits, covering its off-chain relayer network, core smart contracts, and other components, to mitigate some of these risks.
Speed – Cross-chain transfers via Symbiosis can take around 15 minutes, which is much slower than other bridges in the ecosystem.
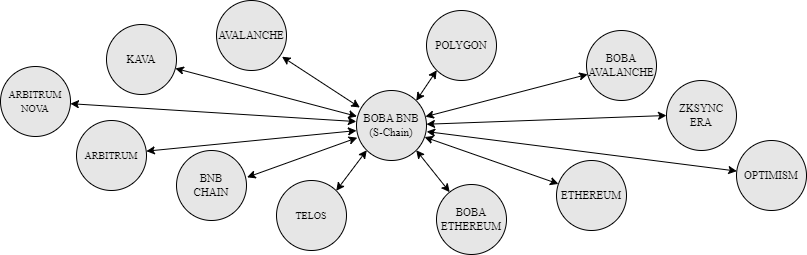
Connectivity – Symbiosis supports over 25 chains, including both EVM and non-EVM chains, and connects with DEXs on these chains to support a wide range of assets.
Statefulness – The Relayer network enables the passing of calldata and the execution of contract calls, a handy feature for facilitating more complex cross-chain actions.
Supported Chains
According to their documentation, the Symbiosis protocol is designed to be compatible with a variety of blockchain types, including:
L1 and L2 blockchains that are EVM-compatible and conform to the required Solidity version.
WASM-based blockchains, such as Near (at the time of publishing, Symbiosis doesn’t support any of this type of blockchain in production. Nonetheless, it’s possible Symbiosis will support them in future updates).
Currently, Symbiosis supports all the major L1s and L2s, with the added support of Tron, setting it apart from other bridges in the market.
Symbiosis has also rapidly supported new L2s such as Mode, Blast, Scroll, and others. This quick expansion into new chains makes Symbiosis a key partner for LI.FI, enabling our partners like Jumper and their users to access these routes through Symbiosis.
Moreover, Symbiosis has strategically integrated Thorchain to enable native BTC cross-chain swaps across 20 chains. They have also been prompt in supporting Bitcoin L2s like Merlin, which are quickly gaining traction.
For the latest updates on the blockchains that Symbiosis protocol supports, please check out the "Supported Blockchains" section in their docs.
Team
Led by a trio of experienced professionals in Will Kamalov (CEO), Nick Avramov (CBDO) and Alexey Lushnikov (CTO), the Symbiosis team is dedicated to providing a user-friendly and secure cross-chain experience. This principle guides the development and operational strategies of the protocol, ensuring that users can seamlessly move around their assets in the multi-chain ecosystem without compromising on security.
Community & Resources
You can learn more about Symbiosis through the following:
You can stay updated about its community by following them on:
FAQ: Symbiosis — A Deep Dive
Get Started With LI.FI Today
Enjoyed reading our research? To learn more about us:
- Head to our link portal at link3.to
- Read our SDK ‘quick start’ at docs.li.fi
- Subscribe to our newsletter on Substack
- Follow our Telegram Newsletter
- Follow us on X & LinkedIn
Disclaimer: This article is only meant for informational purposes. The projects mentioned in the article are our partners, but we encourage you to do your due diligence before using or buying tokens of any protocol mentioned. This is not financial advice.