LI.FI has announced a $29M Series A extension, led by Multicoin and CoinFund. Read Here.

Security Incident Report 16th July
Security Incident
On July 16, 2024, shortly after adding a new smart contract facet, the LI.FI contract experienced a security breach. A vulnerability in this facet allowed the attacker to gain unauthorized access to user self-custodial wallets that had set infinite token approval for the LI.FI contract. The total amount stolen is estimated to be around $11.6 million. The attack occurred on Ethereum and Arbitrum, impacting 153 wallets. Assets drained included USDC, USDT, and DAI. It is important to note that the vulnerability was limited to infinite approvals and did not affect finite approvals, which is the default setting within the LI.FI API, SDK, and widget.
Incident Response
Upon detecting the security breach, our team immediately activated the incident response plan, successfully disabling the vulnerable facet across all chains. This action contained the threat and prevented any further unauthorized access.
Technical Breakdown of the Vulnerability
The exploit occurred shortly after a new smart contract facet was deployed. A vulnerability in the upgrade allowed the attacker to gain unauthorized access to user wallets within minutes of deployment.
The vulnerability stemmed from the fact that callers to the contract were able to make arbitrary calls to any contract without validation. This capability was provided by the LibSwap library, which facilitates making calls to multiple DEXs, fee collectors, and other entities before bridging or sending funds to a user. In all other facets of the LI.FI contract, these calls are validated against a whitelist of approved contract addresses and functions. However, caused by an individual human error in overseeing the deployment process, in the case of the new facet, this validation check was missing.
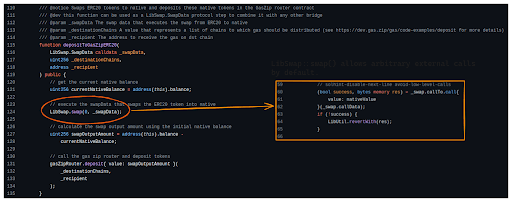
Links to the impacted facet:
New feature that was still in development: https://github.com/lifinance/contracts/pull/700
Facet on Ethereum: https://etherscan.io/address/0xf28A352377663cA134bd27B582b1a9A4dad7e534
Facet on Arbitrum: https://arbiscan.io/address/0xf28A352377663cA134bd27B582b1a9A4dad7e534
Recovery Efforts
Our top priority is recovering user assets. We continue to engage with law enforcement authorities and relevant third parties, including security teams from the industry, to trace and attempt to recover funds drained.
In an effort to support the users affected, LI.FI, with the backing of its major investors, is currently evaluating options to fully compensate affected users as soon as possible.
If you are an affected wallet holder, please complete the following form so that we can get in touch with you directly. Your cooperation is greatly appreciated.
Link to form – users affected by LI.FI smart contract exploit
We are incredibly grateful to the security researchers, @pcaversaccio, @zeroshadow_io, @_SEAL_Org, @0xleastwood, @tracelon_, @hexagate_, @0xVazi, @HypernativeLabs, @invlpgtbl, @Ash42Z, @aliciakatz who continue to assist us in identifying and addressing this issue.
Looking Ahead
LI.FI is strongly committed to the safety and security of our protocol and user assets. In addition to our existing multi-step deployment review process, there are multiple additional security policies and measures in place including:
Multiple audits from a variety of firms
Having an auditing firm on a monthly retainer to review changes at any time
Backend infrastructure & API pen-testing (Whitebox & Blackbox) by an external security firm
Providing bug bounties
An Incident Response Framework
Extensive security assessments of integrated third-party systems
Multiple security policies after NIST
These security policies have been working as designed. As indicated, the incident was caused by an individual human error in overseeing the deployment process. In order to prevent such incidents going forward, we have already started to completely reassess our deployment review process.
We continue to collaborate with security experts to improve our policies. We will provide updates as we make progress. We appreciate everyone's support.
FAQ: Security Incident Report 16th July
Get Started With LI.FI Today
Enjoyed reading our research? To learn more about us:
- Head to our link portal at link3.to
- Read our SDK ‘quick start’ at docs.li.fi
- Subscribe to our newsletter on Substack
- Follow our Telegram Newsletter
- Follow us on X & LinkedIn
Disclaimer: This article is only meant for informational purposes. The projects mentioned in the article are our partners, but we encourage you to do your due diligence before using or buying tokens of any protocol mentioned. This is not financial advice.