Connext.Network — A Deep Dive
All You Need To Know About Connext and XPollinate
Connext is an interoperability protocol that aims to offer a holistic solution for the multi-chain future. With security and decentralization as its core values, Connext offers one of the best bridging solutions in the Web3 ecosystem.
In this article, we will cover the following:
Connext: An Overview
How It Works — Transaction Lifecycle
Bridge Design — Architecture
Transaction Validation Mechanism
Security Model
Incentives
Risks
Supported Chains
Community
Let’s dive in!
Connext: An Overview
Connext was started in 2017 with the following thesis: “Decentralized protocols have the power to put value and ownership back into the hands of individuals. This can only happen if using them is simple enough that they are accessible by anyone.” In 2018, the team at Connext felt that UX was the most significant barrier to the adoption of L2s, so they focused intensely on user experience. Over the years, Connext has built a large community of supporters and stakeholders as they have increased the adoption of Ethereum’s ecosystem through their network of liquidity pools and their increasingly impressive UX.

Connext
Launched in January 2021, Connext is an interoperability protocol that allows users to send fast, fully non-custodial transfers or contract calldata between Ethereum Virtual Machine (EVM) -compatible chains and/or rollups.
It enables users to transfer capital or calldata using its NXTP protocol. NXTP is a trustless, low-cost, and easily extensible base protocol launched in September 2021 with a vision to become the Internet Protocol (IP) of the Ethereum multi-chain ecosystem. According to the team, NXTP has the following distinct advantages over other systems:
Trustless — NXTP does not introduce an external set of validators that control user funds. Instead, the protocol utilizes a lock/unlock mechanism that makes the transfer of funds more secure. This mechanism makes it impossible for user funds to get stolen, even if the transaction validation mechanism defaults.
Extensible — Since the protocol has an extensible architecture and can work the same way on any system, it can be easily expanded to new sidechains, L2s, and other L1 chains. Moreover, given the protocol’s existing liquidity, it can also be extended to build and integrate new kinds of interoperability protocols.
Low-cost — The NXTP protocol was designed to address the scalability and high fees issues associated with the Ethereum network. Since NXTP does not interact with Ethereum L1 when passing through L2s or sidechains, it solves the problems of high gas fees and slow transaction times.
Given its features, Connext has two types of users:
Cryptocurrency Users — Using its network of liquidity pools on different chains backed by routers, Connext allows users to swap value between these pools. This essentially works like AMM DEXes like Uniswap. For instance, if a user has funds on Arbitrum and wants to use an application on Polygon, they can do so by directly calling the contract on Polygon using funds they have on Arbitrum. This way, users can bypass Arbitrum’s 1-week waiting period and L1 fees. Moreover, Connext enables users to do so without relying on any trust assumptions or third-party validators that control their funds.
Developers — Connext offers an SDK that developers can directly integrate into their dApps. This would enable them to utilize Connext’s infrastructure and facilitate cross-chain swaps.
How It Works — Transaction Lifecycle
The Connext network uses NXTP for cross-chain transfers. The NXTP protocol is a smart contract that utilizes a lock/unlock mechanism. This contract has three phases.
Here is a visual representation of the transaction life cycle:

Source: Connext Documentation — Transaction Lifecycle
1. Route Auction — In the first phase, the user broadcasts to the network and signals their desired route to execute the transaction. The routers in the network respond to this broadcast with sealed bids that contain time and price range commitments to fulfill the user’s transaction.
2. Prepare — As the router’s bid is accepted, the auction is completed, and the transaction can be prepared. The user must submit a transaction containing the router’s signed bid to the Transaction Manager contract on the sender-side chain. Doing so will lock the user’s funds on the sending chain.
Once the router detects an event containing the signed bid from the chain, it submits the same transaction to the Transaction Manager on the receiver-side chain, thus locking up the required amount of liquidity. Here, the required amount is the sending amount minus the auction fee given to the Router as a reward for completing the transaction.
3. Fulfill — After detecting that the transaction has been prepared on the receiver-side chain, the user must sign a message and send it to a relayer. Typically, the relayer is another Router that earns a fee for this submission. The role of the relayer is to submit the message received from the user to the Transaction Manager, completing the transaction on the receiver-side chain. By doing so, the relayer unlocks the Router’s locked funds and claims them.
Here, a relayer allows users to submit transactions containing arbitrary calldata without worrying about paying gas fees to do so on the receiving chain. After receiving the signed message, the Router submits it and completes the transaction on the sender-side chain, thus unlocking the original amount.
Bridge Design — Architecture
The Connext infrastructure consists of the following pieces:
Contracts — The funds of all network participants are held in contracts. Moreover, contracts are vital in facilitating the lock/unlock mechanism NXTP protocol uses based on the data submitted by users and routers.
Subgraphs — By caching on-chain data and events, subgraphs enable scalable querying or responding.
SDK (Users) — Users on the network are responsible for creating the auctions, listening for events, and creating transactions on the user-side chain.
TxService — Continuously attempts to send transactions to the chain.
Messaging — The messages are responsible for sending data about the preparation, status, and transfer of funds and calldata.
Router — The routers on the network listen for events from the messaging service and subgraph. Based on these messages, they dispatch transactions to the txService.
Here’s a visual representation of Connext’s architecture:
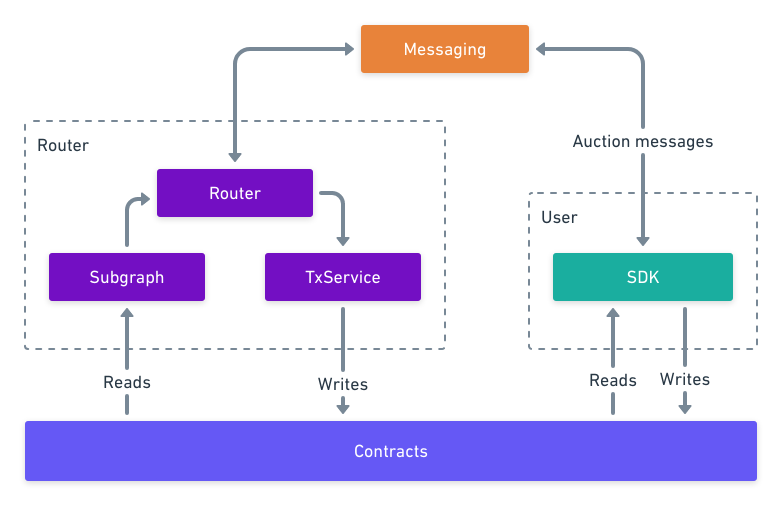
Source: Connext Documentation — How It Works
Based on the factors mentioned below, we can evaluate Connext’s architecture and design as follows:
Security — User funds can never be lost or stolen as Connext’s security is equal to the underlying protocol it is bridging. Thus, it reduces the trust assumptions involved.
Speed — Connext can execute transactions at high speeds because it utilizes locally verified systems. For instance, in the data set, we found that out of the 50,732 transactions conducted on Connext using Li.Finance’s infrastructure, 91% have taken below 1 hour to be finalized.
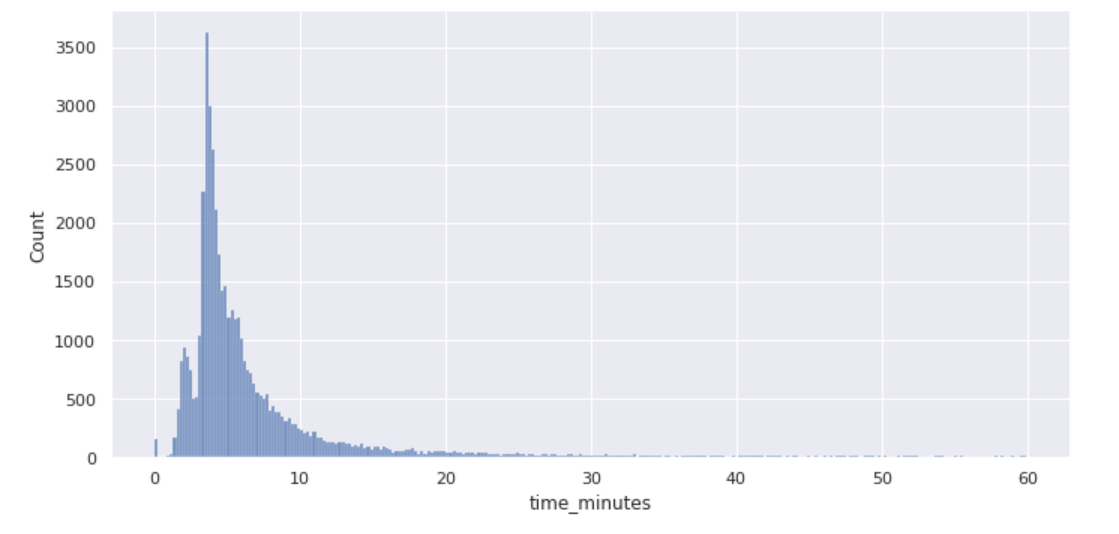
Bridge Evaluation: Speed
Connectivity — Connext has good connectivity as it supports a wide range of destination chains.
Capital Efficiency — Compared to other solutions, Connext is very capital-efficient considering its significant amount of economic throughput.
Statefulness — The trade-off of capital efficiency is statefulness. While Connext can pass around calldata, it is limited in its ability to transfer specific assets and execute cross-chain contract calls. However, it’s important to note that NXTP and Connext still allow for some statefulness.
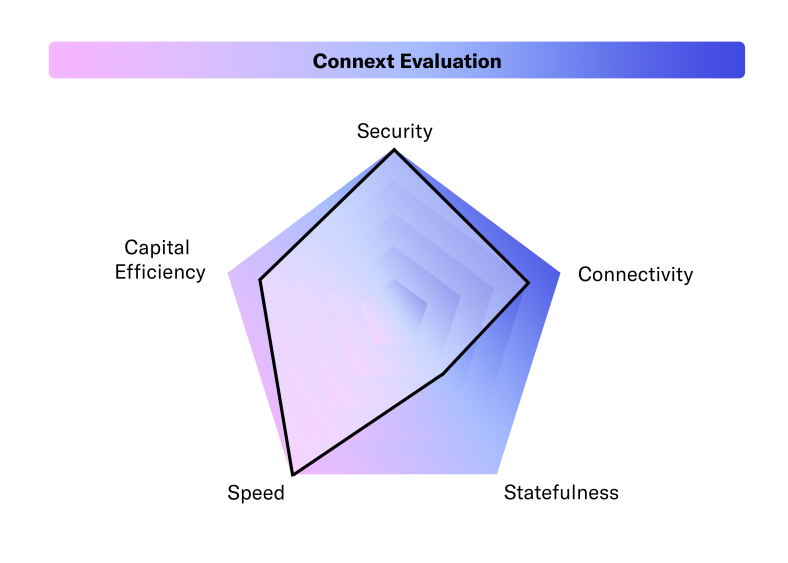
Connext Evaluation
Transaction Validation Mechanism
To validate cross-chain transactions, Connext uses a pool of liquidity networks backed by routers. This offers the following benefits:
Enhanced security — Connext network will not be any less secure than underlying blockchains because it leverages their security.
Funds are never lost — Users’ funds will never be lost since the network uses a lock/unlock mechanism that ensures that routers cannot steal them.
Native assets — The assets provided by the routers are native to the destination chain instead of being derivative assets. As a result, these assets are fungible.
Security Model
Connext adopts the same core security model as the one used by other locking systems such as Hashed Timelock Contracts (HTLCs). This type of security model offers the following benefits:
Time-bound transactions — Connext’s infrastructure guarantees the timely execution of transactions. This ensures that users know the maximum amount of time a transaction has to go through. If a transaction is not completed within this period for any reason — malicious or non-malicious — the transaction is stopped, and the user safely recovers their funds.
Minimizes counterparty risks — Since the settlement of each transaction is assured, the counterparty risks are reduced since the ‘what-ifs’ of a transaction have been removed. Thus, by creating a time-based escrow, Connext’s security model reduces counterparty risks in their contracts.
Incentives
The Connext system uses routers to provide liquidity and relay calldata between chains to execute swaps. The routers earn a fee for each transaction that they facilitate.
Risks
Interacting with Connext Bridge has the following risks:
Loss of funds — User can lose their funds in the Connext system in the following scenarios: ▪ The system’s code is hacked. ▪ The user makes an error. ▪ The chain is attacked, creating the possibility that the routers lose funds. ▪ The user does not properly verify that the correct amount of funds/transaction data has been prepared on the receiving chain. However, it is important to note that the Connext SDK automatically takes care of this for both users and developers.
DoS and griefing — If a Router with malicious intent commits to executing a transaction but does not submit a corresponding prepare-transaction on the destination chain, user funds may get locked up for the duration of the expiry. In the future, Connext plans to explicitly penalize such malicious actions from routers via slashing.
Centralized router network — According to Connext’s technical documents, the Connext team is working closely with a whitelist of routers that only the team can update. This approach is temporary and was a recommendation by Connext’s security auditors. The team plans to implement a slashing mechanism in the future. For now, there is a risk of the router network being centralized and thus attempting to grief users if they wish to.
Censorship risk on messaging — In the initial stages, the messaging infrastructure of the network is being hosted by the Connext team. This places significant reliance on the team to maintain high uptime on the infrastructure and thus introduces a risk of censorship by the team. However, it is important to note that the Connext team is working on removing this risk in the coming months.
Technology Risks — While the Connext infrastructure has been audited, it is still susceptible to technological risks, given the nature of the operation.
Supported Chains
Given its extensible nature, Connext is very easy to support on any chain. However, the process of integrating with Connext differs based on whether or not the chain is EVM-compatible.
EVM-Compatible — These chains can reach out to the Connext team with their Discord server if they wish to get contracts deployed on their chain.
Non-EVM-Compatible — These chains can build support for Connext by porting the contracts and rewriting them to the network’s txService.
It is important to note that users will only connect to Connext-supported chains that have liquidity provided to them from routers.According to Connext Documentation, currently supported chains include the following:
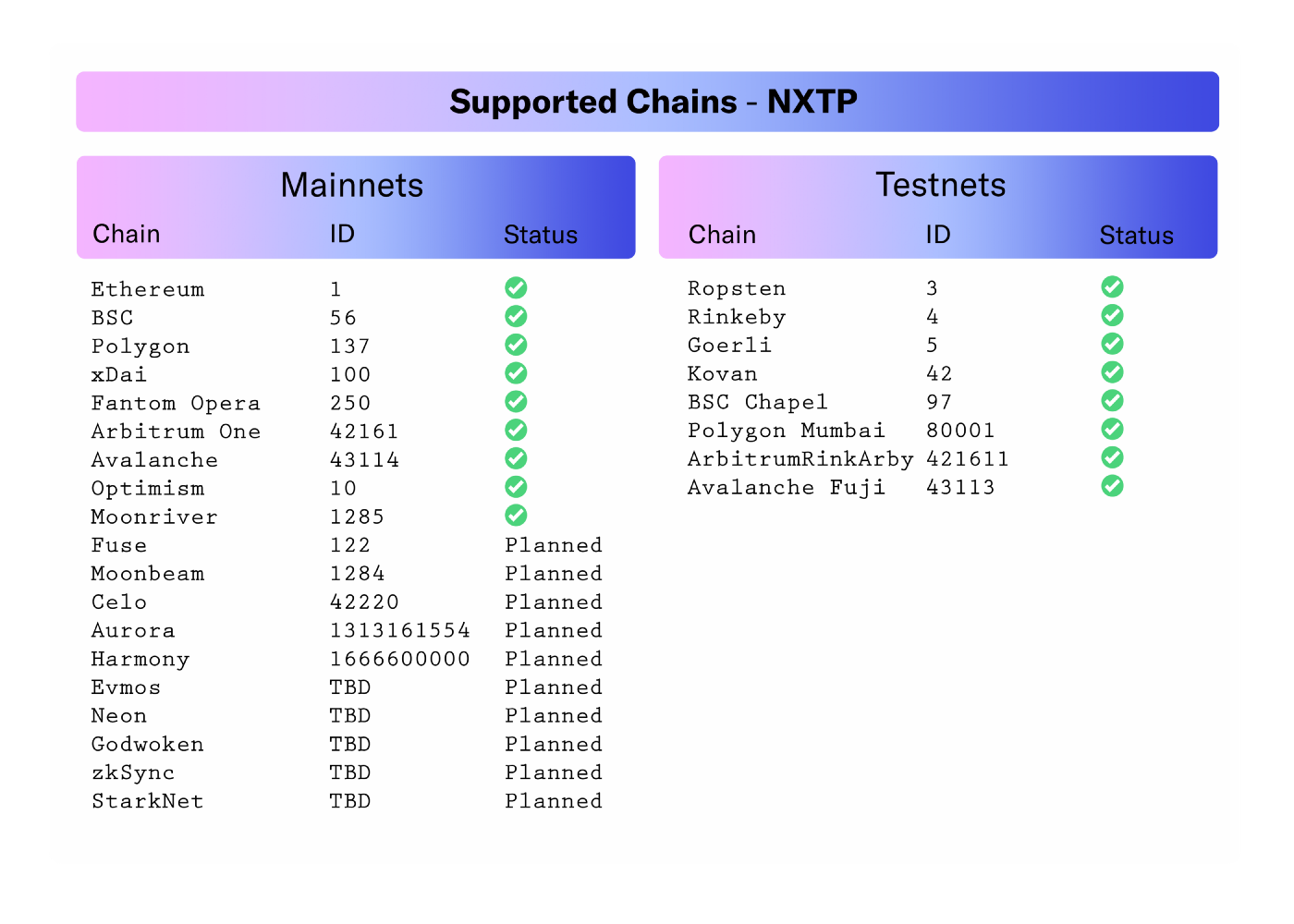
Supported Chains — NXTP
From the chains mentioned above, Li.Finance’s infrastructure supports Ethereum, Fantom, xDai, Polygon, Binance Smart Chain, and Arbitrum.
Team
Led by co-founders Arjun Bhuptani, Rahul Sethuram, and Layne Haber, the team at Connext was one of the first teams to work on L2 research. Their goal has always been to improve the user experience of Ethereum and the broader Web3 ecosystem. The team believes that decentralized networks will transform Finance and give value back to the users.

The Backers
Community
You can stay updated with Connext and its community through the following:
To facilitate the development of the multi-chain ecosystem, the Connext team is also accepting ‘Requests For Proposals.’ The team is looking for developers and applications that want to build things through Connext and foster the development of the ecosystem. If you’re interested, you can check out the bounties here.
Closing Thoughts
At LI.FI, we believe Connext offers one of the best bridges in the ecosystem. This is because of the following reasons:
Connext has a strong core team with years of experience working in the crypto ecosystem, especially on Ethereum. In fact, their team was one of the first teams to work on layer 2 research.
Connext is building for the long-term with security and decentralization at its core. The team focuses on trustlessness and is working on creating a holistic solution that can function well for years to come.
The team talks openly about the trade-offs they have made in order to align with their values. Their deep dive on the ‘Interoperability Trilemma’ talks about how they are currently trading off the generalizability aspect.
The team has a long-term plan to overcome the current trade-offs — Taking inspiration from Ethereum’s modular architecture, Connext plans to solve the interoperability trilemma by creating a composable stack of different protocols on top of it.
Given the above reasons, Connext was the first bridge that we integrated on Li.Finance. We believe the vision and values of both teams are aligned towards creating a sustainable solution for the multi-chain future. Together, we look forward to enabling the seamless cross-chain flow of value and data.
FAQ: Connext.Network — A Deep Dive
Get Started With LI.FI Today
Enjoyed reading our research? To learn more about us:
- Head to our link portal at link3.to
- Read our SDK ‘quick start’ at docs.li.fi
- Subscribe to our newsletter on Substack
- Follow our Telegram Newsletter
- Follow us on X & LinkedIn
Disclaimer: This article is only meant for informational purposes. The projects mentioned in the article are our partners, but we encourage you to do your due diligence before using or buying tokens of any protocol mentioned. This is not financial advice.