What Are Blockchain Bridges And How Can We Classify Them?
Classifying Bridges As We Know Them
The Crypto ecosystem has evolved rapidly over the last decade. Ever since the release of the Bitcoin whitepaper in 2008, there has been tremendous innovation in the space and widespread, almost mainstream, adoption. While every year in crypto is unique, 2021 changed the ecosystem in ways that have people interested in crypto’s seemingly limitless future.
2021 was the year of the L1s — which resulted in many predicting a multi-chain future for crypto, as opposed to a winner take all stance that many had prior to the rise of these blockchains. However, with the drastic increase in the number and size of different blockchain ecosystems, there is now a need for key infrastructure to connect them. This is where blockchain bridges come in.
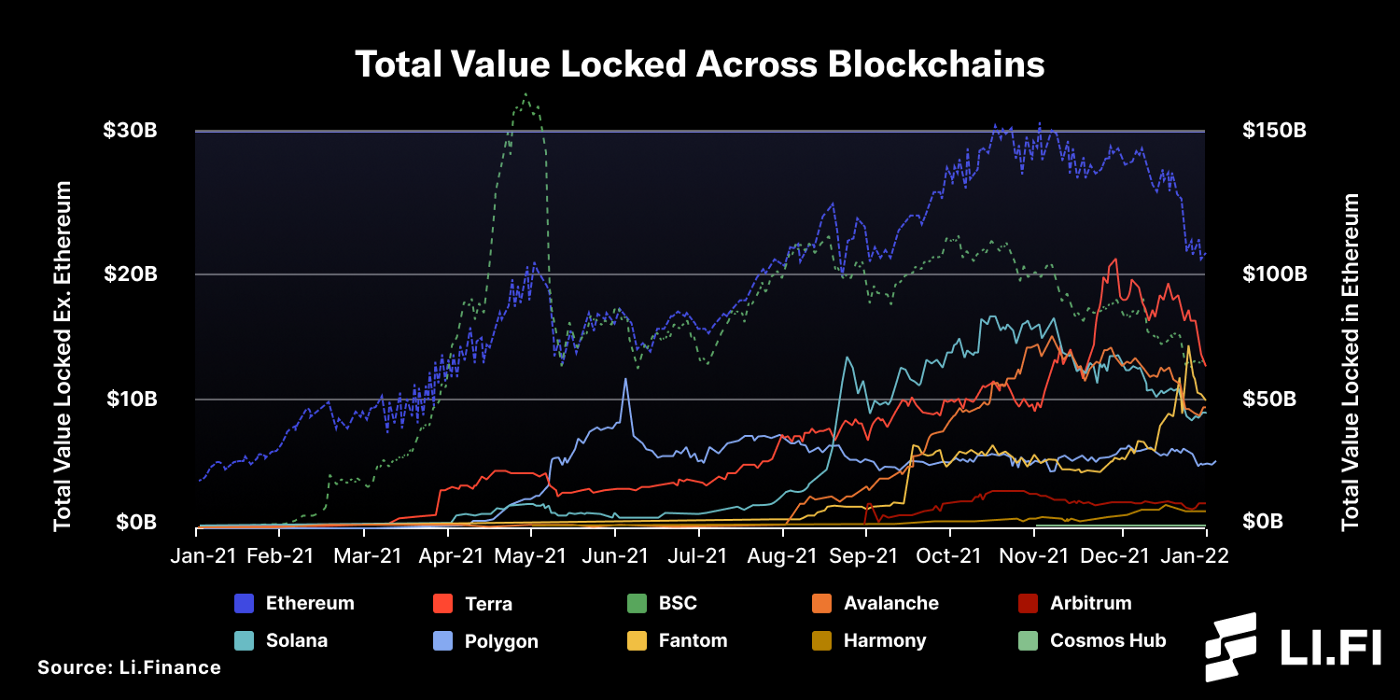
Ethereum still dominates but other chains are growing (Data Source: DeFi Llama)
Here, we will talk about:
What Is A Blockchain Bridge?
Why Do We Have Different Types Of Bridges?
How do we classify bridges?
Let’s dive in!
What Is A Blockchain Bridge?
Blockchain bridges work similarly to real bridges in the physical world. However, instead of connecting physical locations, bridges in crypto connect two different blockchains. This connection is important because, without a bridge, blockchains are siloed environments that cannot communicate with each other. This is because each network has its own set of rules, governance mechanisms, native assets, and data that are incompatible with the other blockchains. However, with a bridge between two blockchains, it becomes possible to transfer crypto-assets and arbitrary data between them. Thus, bridges are key for interoperability in the crypto ecosystem and are necessary to make different blockchain networks compatible with each other.
Let’s take an example:
Alice has ETH on Ethereum Mainnet and wants to use it on Avalanche. These two chains have their own protocols, rules, communities, and consensus mechanisms and thus, interoperability between them is not possible. In such a case, something needs to go in the middle and offer a way to take information from the Ethereum Mainnet to Avalanche. To do so, Alice would most likely transfer assets via a blockchain bridge in order to securely move the ETH from Ethereum Mainnet to Avalanche. Using the bridge, Alice will be able to convert ETH on Ethereum to wETH on Avalanche.
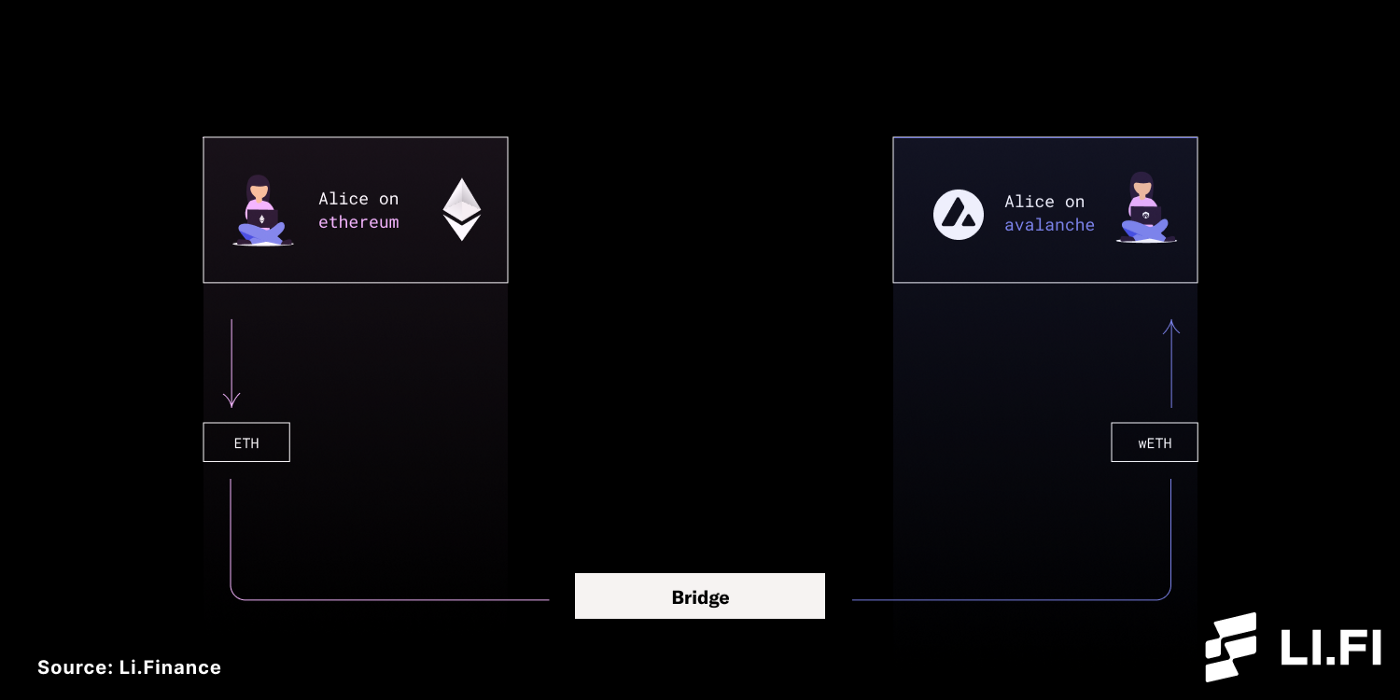
Bridging ETH from Ethereum Mainnet to Avalanche (ETH to wETH)
Why Are There Different Types Of Bridges?
Bridges essentially enable communication between different blockchains. And, just like with complex math problems, when you take a look at different bridging solutions in the crypto ecosystem, you will find that there is no one way of enabling communication between blockchains. Bridges have different designs with unique strengths and trade-offs, and thus, there are a plethora of options when it comes to which bridge can be used to communicate between two blockchain networks. Let’s dig a little deeper into how communication works.
Bridges work by establishing communication channels between two blockchains. In an ideal world, blockchains would just talk to each other but in reality, that’s not possible because one blockchain doesn’t store the state of the other.
Let’s take an example:
A dApp on Ethereum wants to communicate with a dApp on Solana. Due to the trust boundaries between Ethereum and Solana, they cannot simply talk to each other. These trust boundaries include but are not limited to:
Ethereum and Solana don’t know about each other.
Both can only know what’s happening on their own chain and have no idea what’s going on off-chain.
To both the blockchains, receiving a message from the other is like having an interaction with the outside world that they know nothing about. Hence, trust cannot be established to validate these messages.
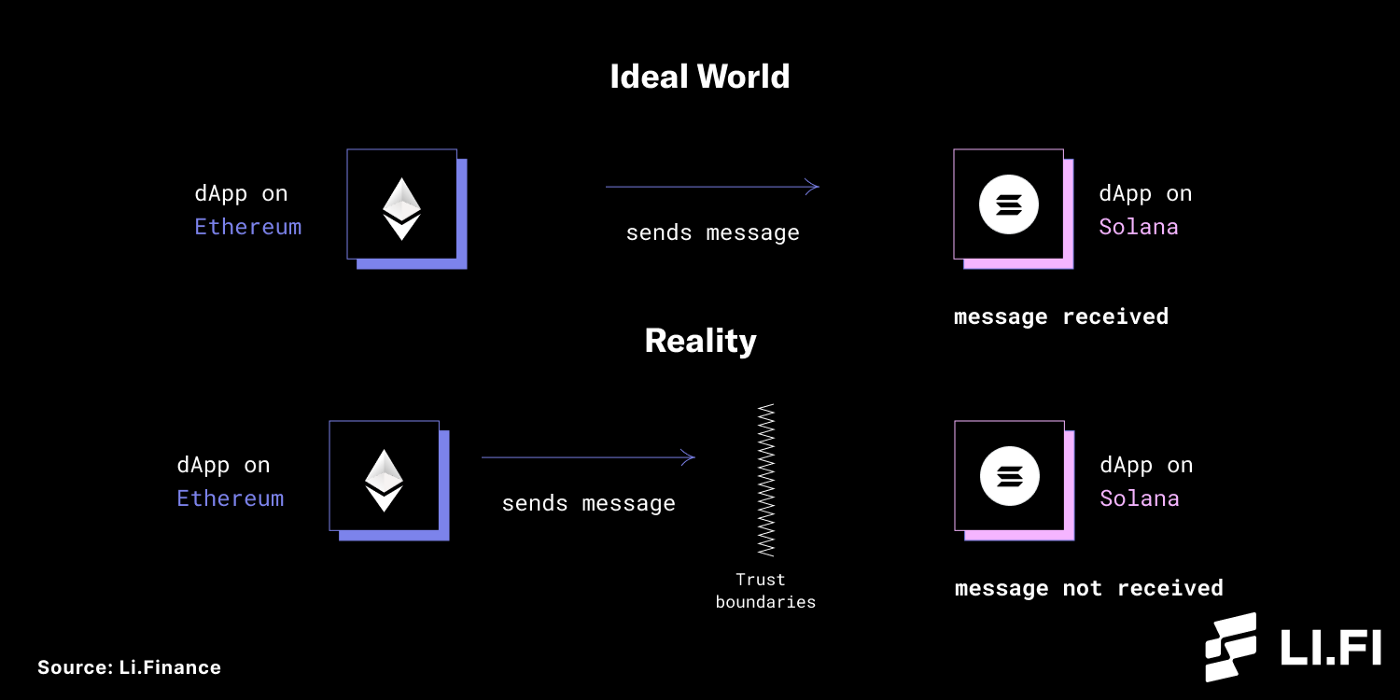
Ideal World Vs Reality
Moreover, blockchains can only send messages in one direction. That is to say, there is only one-way communication across a channel. One blockchain can send a message to another on one channel, but there’s no way for the other blockchain to reply on the same channel and confirm that the message has been received.
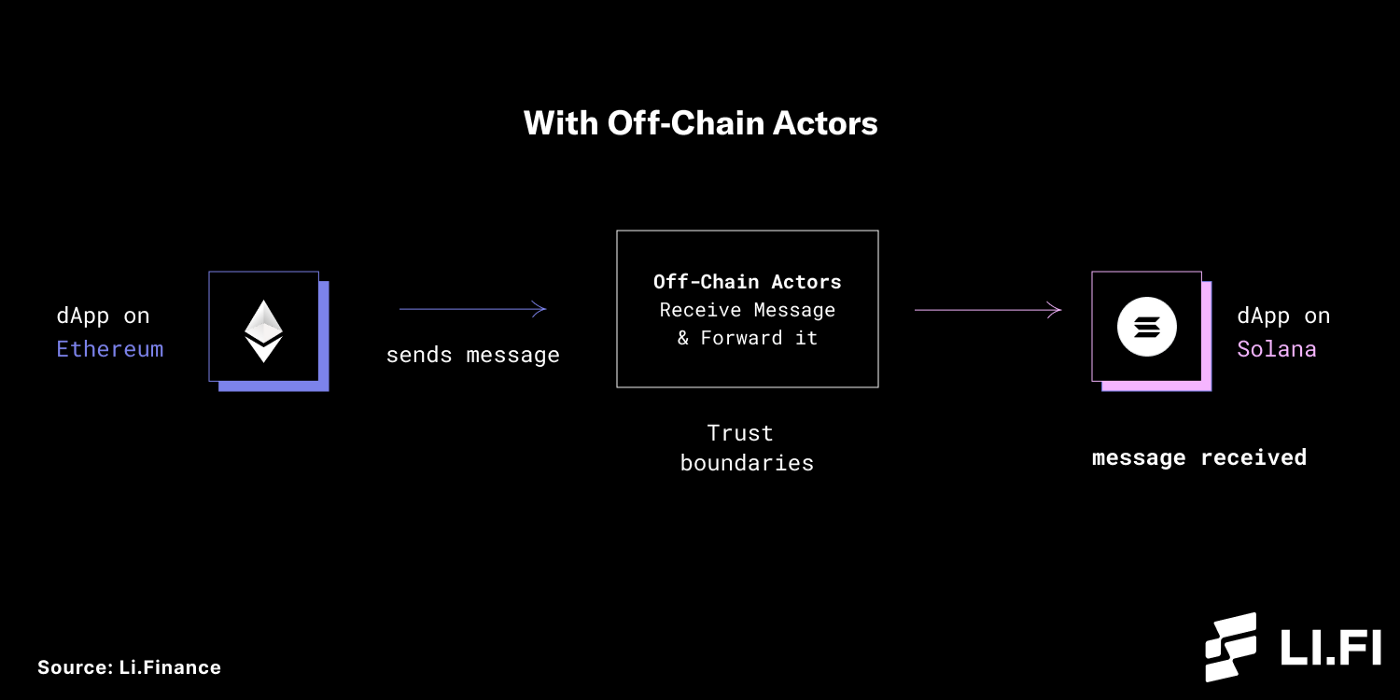
To establish trust between blockchains and make two-way communication possible, we need something in the middle, something that can bridge the gap between these blockchains. This is where blockchain bridges make it possible to not only transfer messages, data, and resources between different blockchains but also make cross-chain asset transfer. This changes things, as blockchains are no longer limited to one-way communication, as bridges enable them to communicate with other blockchains back and forth.
Bridges use different mechanisms, or actors, that play the role of verifiers between blockchains to enable communication and overcome the trust boundaries. Without these off-chain actors, communication between blockchains will not be possible.
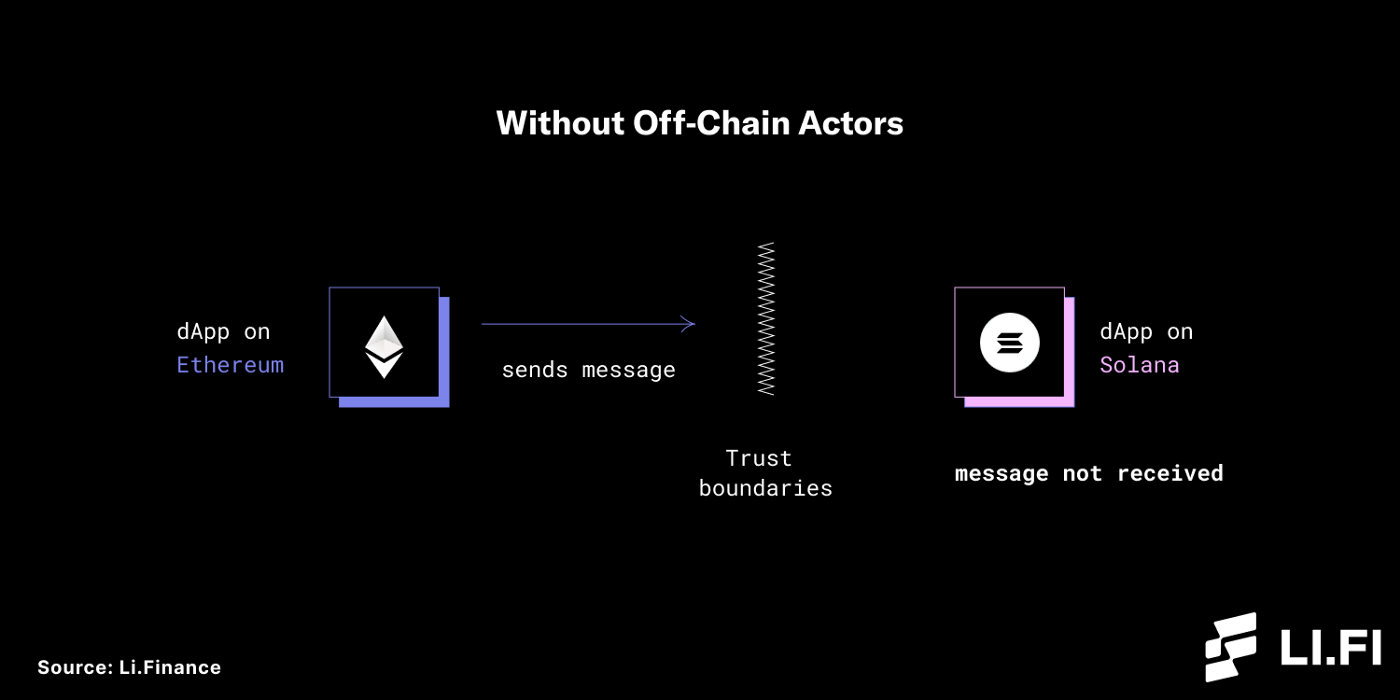
However, with these off-chain actors acting as the ‘man-in-the-middle’ of the two blockchains, trust boundaries can be overcome, and communication becomes possible.
The role of verifiers is the main differentiator in how bridges work. Essentially, some bridges use a trusted system and others use a trustless system of verifiers. Moreover, we see different types of bridge designs because of the interoperability trilemma in the crypto ecosystem. The interoperability trilemma states that “interoperability protocols or bridges can only have two of the following three properties:
Trustlessness: having equivalent security to the underlying domains.
Extensibility: able to be supported on any domain.
Generalizability: capable of handling arbitrary cross-domain data.”
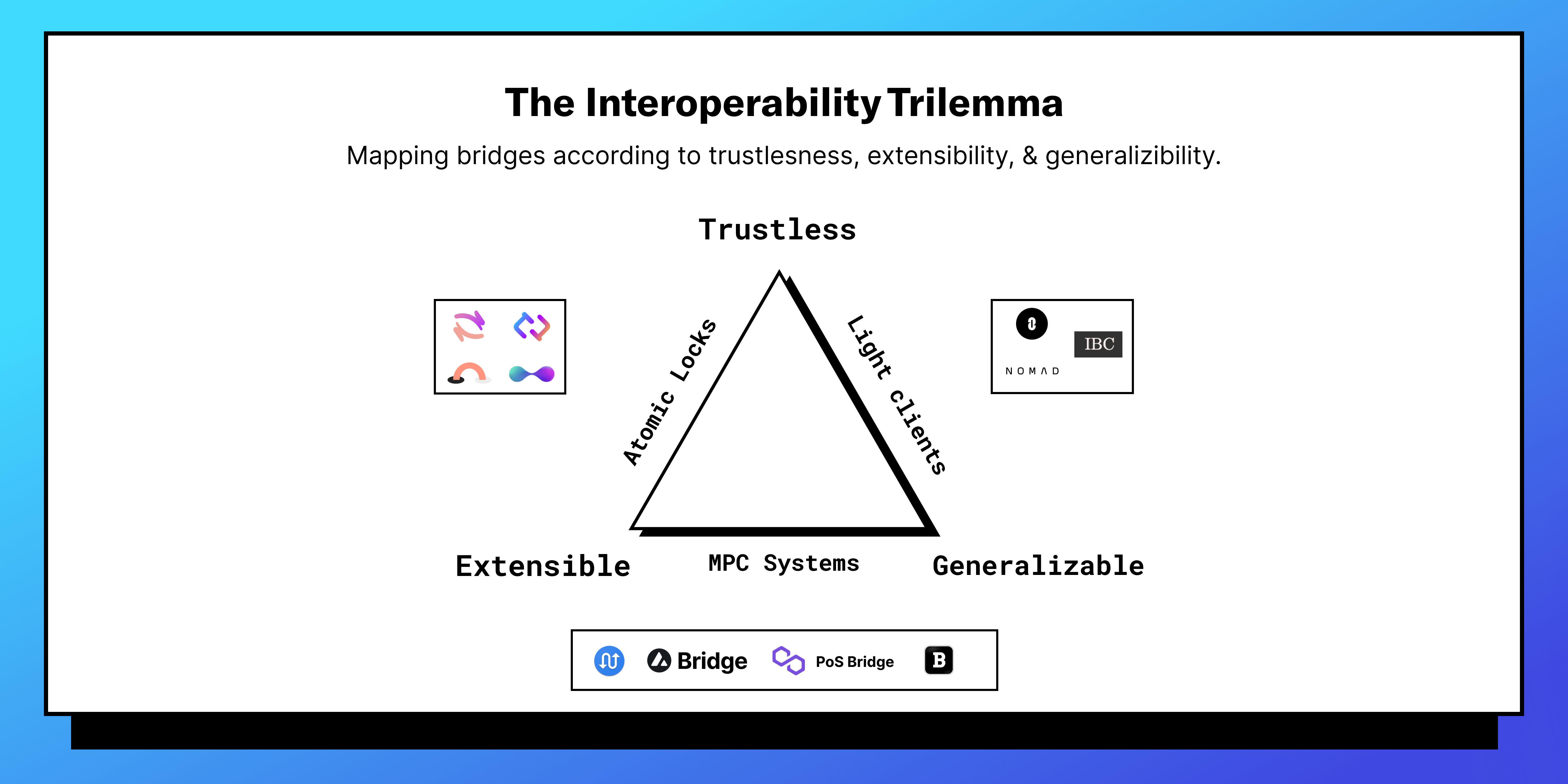
Mapping bridges according to trustlessness, extensibility, and generalizability.
Also, in his article, Arjun Bhuptani classifies bridges based on how they are verified into natively, externally, and locally verified systems. Different bridging solutions focus on different factors out of the three listed above and have their own strengths and trade-offs. As a result, there are varying bridge designs with unique value propositions.
The above points explain why we have different bridge designs. But, in general, we see different types of bridges because of what they connect and their main use-cases. We will further explore this in the “Classification Of Bridges Based On Their Functionality” section.
Classification Of Bridges Based On How They Work
While the purpose of all blockchain bridges is the same (i.e., enabling communication between different blockchains) the way they go about doing so varies. Based on how they work, bridges can generally be classified into:
Trusted Bridges — These bridges use a central authority for their operations. They are called “trusted bridges” because users need to trust a third party to use the bridge and hold their funds. Examples of trusted bridges include Multichain and chain-specific bridges like Binance <> Ethereum bridge.
Trustless Bridges — These bridges remove the role of the trusted third party through the use of smart contracts and algorithms. They are called trustless bridges because they don’t require the users to trust a central authority for using the bridge. Hence, the security of their funds always remains in the custody of the user. Examples of trustless bridges include Connext, Hop, and other bridges with a simple atomic swap mechanism.
Let’s take an example:
Imagine you’re at the airport security checkpoint. There are two types of checkpoints:
Manual Checkpoints — These are controlled and operated by officials whom users have to trust with their personal information and belongings.
Self Check-In — These are operated by machines and users always remain in control of their personal information and belongings.
Manual checkpoints are trusted bridges.
They depend upon a trusted third party, that is to say, the officials for their operations. Users have to give up control of their assets.
Manual checkpoints are trusted bridges
Self check-ins are trustless bridges.
They remove the official’s role with technology and enable users to remain in control of their assets.
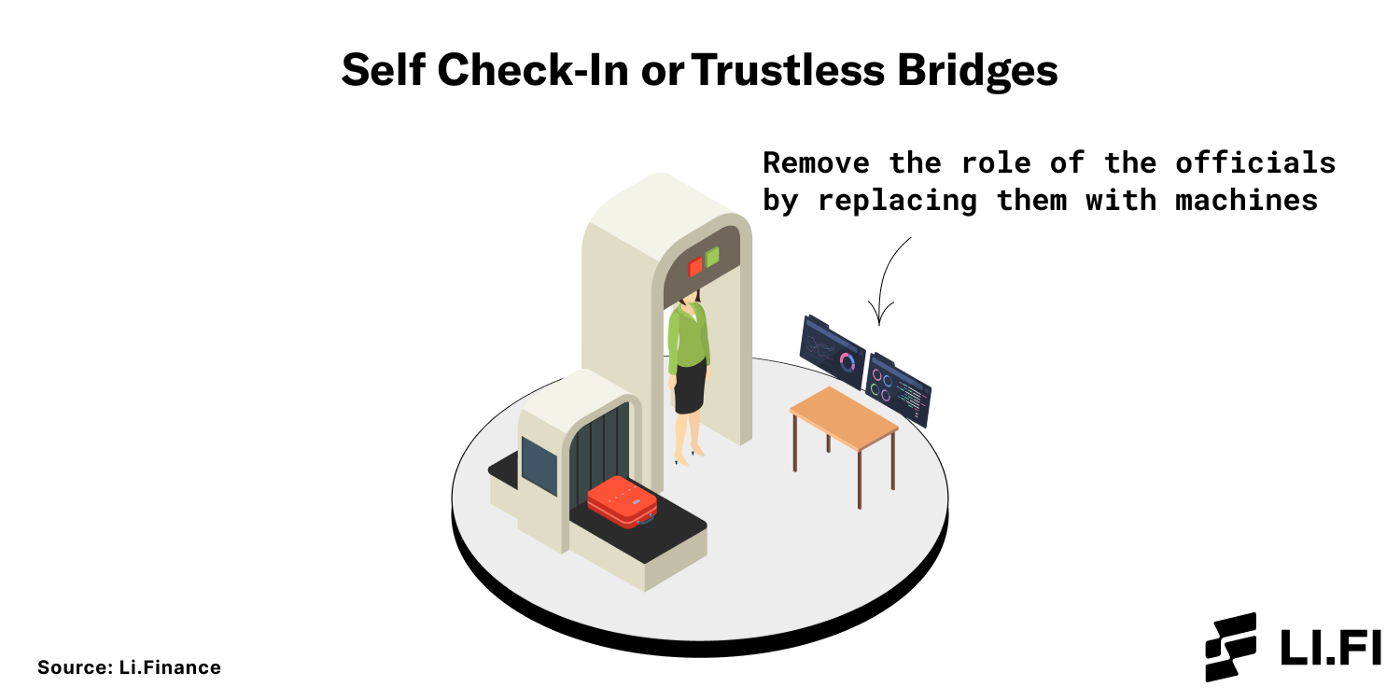
Self check-ins are trustless bridges
Classification Of Bridges Based On What They Connect
In addition to how they work, bridges can also be classified on the basis of what they connect into the following categories:
L1 <> L1 Bridges — These bridges connect different L1 blockchains with each other. For example, the Avalanche Bridge (AB) connects Ethereum and Avalanche.
L1/L2 <> L2 Bridges — These bridges connect the Mainnet with different L2 solutions and the L2s with each other. For example, Across is a bridge that connects Ethereum Mainnet to L2s like Arbitrum and Optimism. Hop Protocol is a bridge that connects different L2s with each other in addition to connecting the Ethereum Mainnet with them.
Let’s take an example:
Building on Haseeb Qureshi’s mental model describing blockchains as cities, we can say that bridges are like roads that connect different cities. Based on what they connect, roads can be classified into the following:
National Highways — These are the roads that connect all major cities.
State Highways — These are the roads that connect significant parts within the city.
National Highways are L1<>L1 bridges.
If Ethereum is New York City and Avalanche is Chicago, the Avalanche Bridge (AB) is the National Highway that connects both cities.
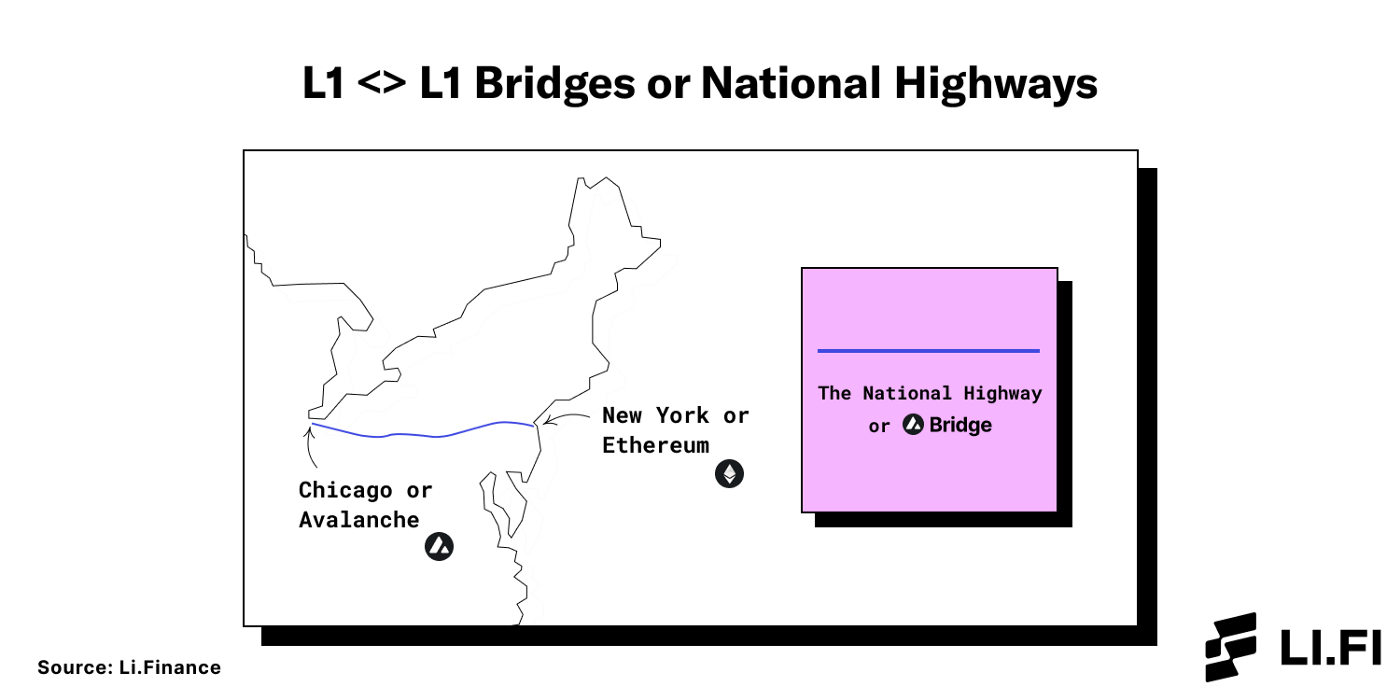
National Highways are L1 <> L1 bridges.
State Highways are L1/L2 <> L2 bridges.
If L2s and rollups like Arbitrum and Optimism are two skyscrapers on Ethereum, that is to say, in New York City, Hop Protocol is the state highway that connects them.
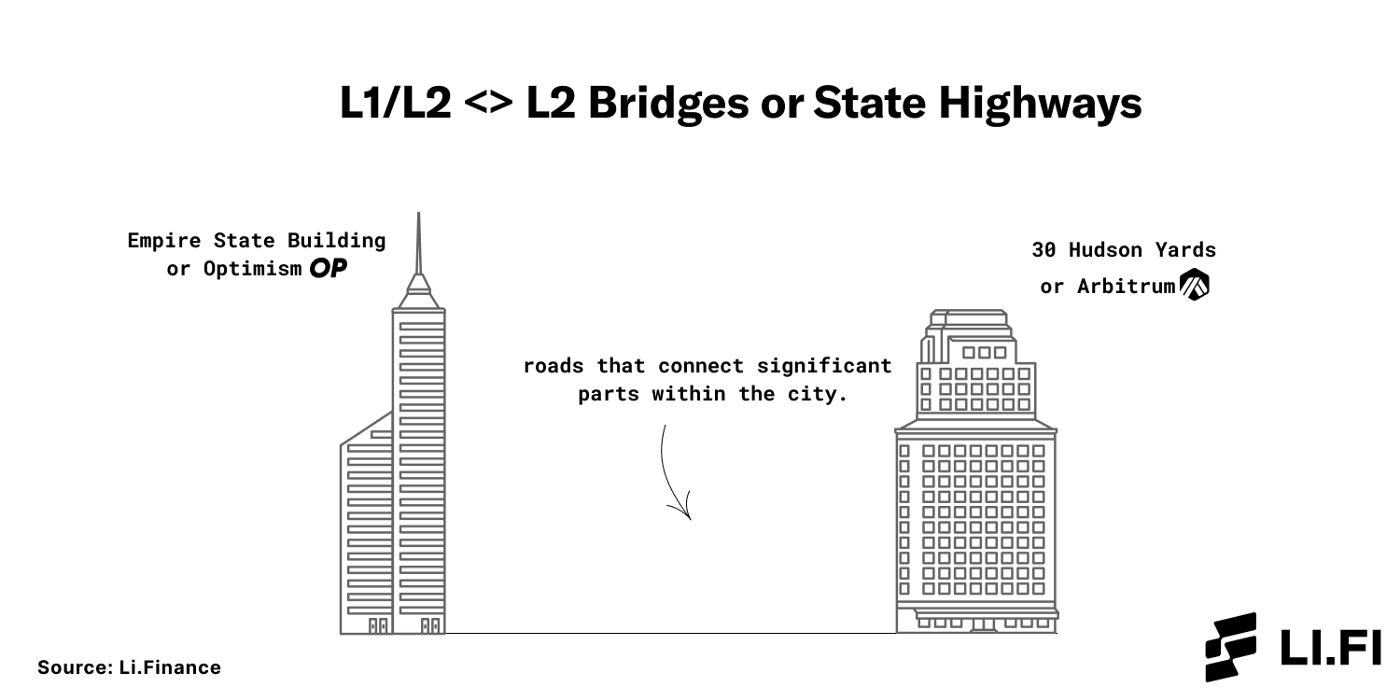
State Highways are L1/L2 <> L2 bridges
Classification Of Bridges Based On How They Move Assets
Bridges can also be classified based on the mechanism they use to move assets across chains. Generally, based on how they move assets, bridges fall into the following buckets:
Lock & Mint — These bridges lock assets on the source chain and mint assets on the destination chain. Examples: Polygon’s PoS bridge, Avalanche Bridge (AB), wrapped BTC, wMonero.
Burn & Mint — These bridges burn assets on the source chain and mint assets on the destination chain. Examples: Circle's CCTP, LayerZero's OFTs, Wormhole's xAssets.
Atomic Swaps — These bridges swap assets on the source chain for assets on the destination chain. Generally, they are more trustless because they rely on self-executing smart contracts for asset swaps and remove the requirement for a trusted third-party necessary in lock & mint or burn & mint mechanisms. Examples: cBridge, Connext, Across.
Let’s take an example.
Imagine you’re traveling in your car from City A to City B which is connected by a bridge. When you reach the bridge, ready to leave City A for City B, you have 3 options to cross the bridge:
Leave your car in a warehouse in City A and, in return, you’ll get an identical car in City B. When you return to City A, you can simply return the car in City B you got on arrival and take your original car back. This is similar to the lock and mint mechanism used by bridges.

Lock & Mint Bridges
To leave City A, you must destroy your car and in return, you will get an identical car in City B. When you return to City A, the same process will be followed again — you must destroy your car in City B and you will get an identical car in City A. This is similar to the burn and mint mechanism used by bridges.

Exchange your car in City A for another car in City B. When you want to return to City A, you can follow the same process again — exchange your car in City B for another car in City A. This is similar to the atomic swaps mechanism used by bridges.
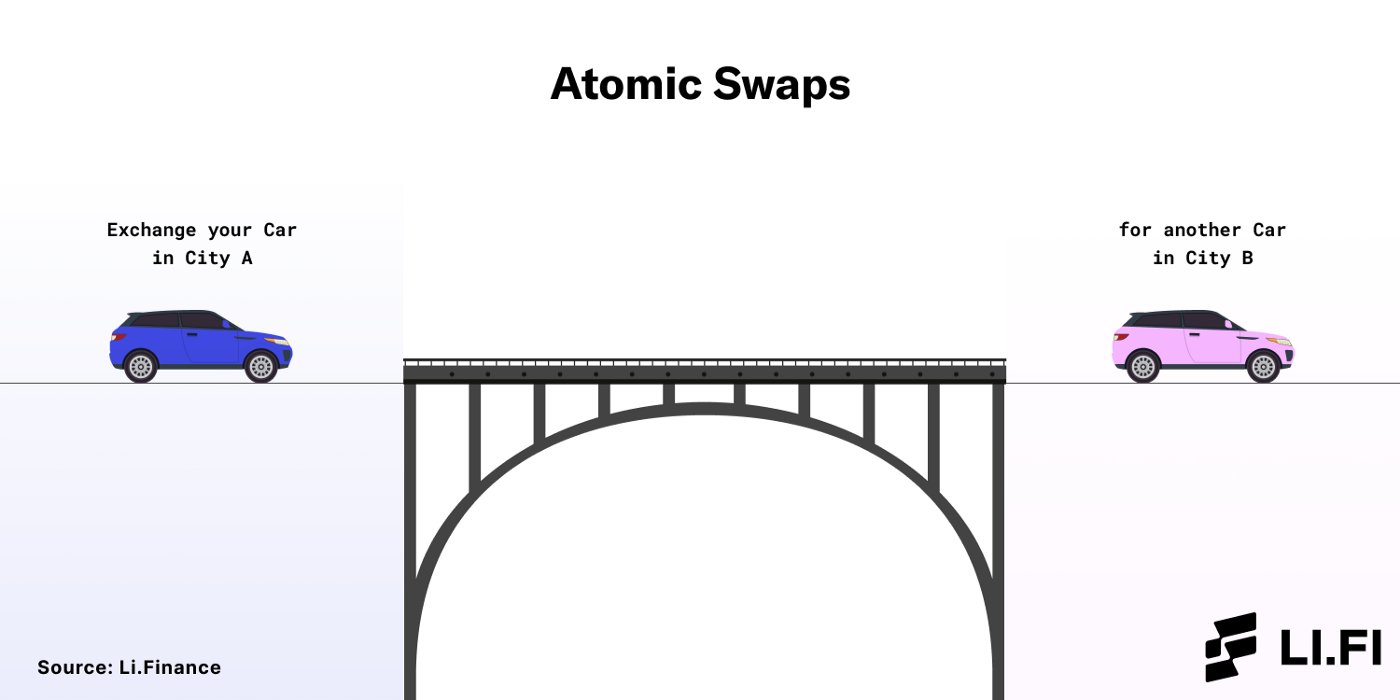
Atomic Swaps
Classification Of Bridges Based On Their Function
The classifications mentioned above differentiate between bridges very broadly. Things can get complicated when looking into different bridge types and designs based on how bridges are used (this to say, their function). Based on functionality, bridges can be classified into the following:
Chain-To-Chain Bridges — These bridges are mainly designed to support the movement of assets between two blockchains. Generally, such bridges use the lock and mint mechanism. Examples: Native bridges such as Polygon’s PoS Bridge, Binance <> Ethereum Bridge, Avalanche Bridge (AB).
Multi-Chain Bridges — These bridges are designed for transferring assets across multiple blockchains. They are built such that they can be deployed to any kind of L1 or L2 blockchains. Examples: Connext, cBridge, Across.
Specialized Bridges — These bridges are focused on specific ecosystems and are designed to support the movement of assets across focused regions. Due to specialization, these bridges are generally able to facilitate faster and cheaper cross-chain transactions. Examples: Hop is a rollup-to-rollup bridge that enables the transfer of assets across the Ethereum Mainnet and L2s whereas Across is a bridge that focuses on enabling the quick and cheap transfer of assets from L2 rollups to Ethereum Mainnet.
Wrapped Asset Bridges — These bridges are designed specifically to enable the transfer of non-native assets to different blockchains. They do so by creating wrapped assets on the destination chain representing the original asset on the source chain. Examples: wrapped BTC, Interlay, wMonero.
Data Specific Bridges —These are interoperability protocols designed specifically for transferring arbitrary data across multiple blockchains. Generally, these protocols become the base layer for dApps and make it possible for them to achieve cross-chain composability. Examples: Celer’s inter-chain Message Framework, IBC, Nomad, Data Movr.
dApp Specific Bridges — From a purely technical perspective, these are not bridges. By connecting to different blockchains, these dApps have built an ecosystem that allows value to be transferred across blockchains in a manner similar to bridges. Examples: Thorchain is a decentralized cross-chain AMM that offers cross-chain liquidity features that enable the exchange of assets across blockchains. Other examples include Anyswap, Wanchain, and Synapse.
Closing Thoughts
The one size fits all approach doesn’t apply to bridges. There is no perfect solution; there are only trade-offs that are made for specific use cases — Each bridge has its own strengths and weaknesses, and as we learned from the interoperability trilemma, all bridges have to choose between trustlessness, extensibility, or generalizability.
The multi-chain is well and truly upon us. Today, we have over 50 unique bridges crisscrossing the cryptoverse. At LI.FI, our goal is to completely abstract away the complicated process of bridging assets. We want users and developers to focus on leveraging the limitless potential of blockchain technology rather than getting bogged down in the details of deciphering the difference between the various types of bridges.
We’ve partnered up with the brightest minds and aim to build the best abstraction and aggregation solution available on the market. If you’re a blockchain network, bridge builder, or dApp developer, come talk to us and let’s work together!
FAQ: What Are Blockchain Bridges And How Can We Classify Them?
Get Started With LI.FI Today
Enjoyed reading our research? To learn more about us:
- Head to our link portal at link3.to
- Read our SDK ‘quick start’ at docs.li.fi
- Subscribe to our newsletter on Substack
- Follow our Telegram Newsletter
- Follow us on X & LinkedIn
Disclaimer: This article is only meant for informational purposes. The projects mentioned in the article are our partners, but we encourage you to do your due diligence before using or buying tokens of any protocol mentioned. This is not financial advice.